A week or two ago there was a spate of stories about big-name US newspapers like the Wall Street Journal and New York Times getting hacked by the Chinese. I thought it was pretty noteworthy, and I was going to put up a note when I got distracted by other things.
Then it all went to Hell.
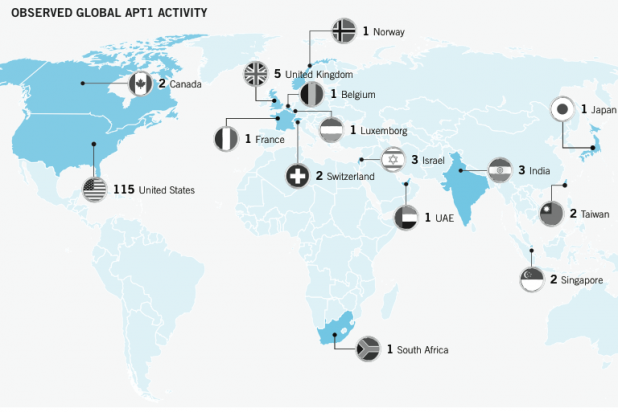
It’s been an open secret for quite some time that the Chinese military are behind an onslaught of cyber attacks on US soil, but outside of tech security circles you probably didn’t hear very much about it. This all changed when US cyber security firm Mandiant issued a scathing report linking the attacks (perpetrated by a group known as “APT1”) with a specific unit within China’s People’s Liberation Army: unit 61398.
Mandiant’s report, summarized via Slashdot, specified that:
“Since 2006, Mandiant has observed APT1 compromise 141 companies spanning 20 major industries,” the report continues. “APT1 has a well-defined attack methodology, honed over years and designed to steal large volumes of valuable intellectual property.” APT1 has the ability to access victim networks for an average of 356 days, stealing terabytes of compressed data during that period.
Sound ominous? It should. So what’s the point of all this hacking?
Information stolen by the group includes manufacturing procedures, business plans, policy positions and analysis, emails of high-ranking employees, user credentials, and product development and use. However, Mandiant lacks “direct evidence” about who ends up receiving that information, or how all that data is processed into a usable form.
Now that Mandiant has specified the exact military unit responsible for the attacks, the mainstream press is free to go to down with very detailed stories. The New York Times has a story featuring a photo of the exact building from which the attacks are claimed to be originating, a 12-story office building staffed by hundreds or even thousands of hackers and their support crew of linguists and researchers.
Even more detailed than that, Mother Jones has a report of three individual hackers that Mandiant has uncovered three of the individual hackers (Jack Wang, a.k.a. Wang Dong, a.k.a. UglyGorilla, DOTA, a.k.a. Rodney, a.k.a. Raith, and Mei Qiang, a.k.a. SuperHard). Mandiant’s Threat Intelligence Center has even posted a YouTube video showing “a live, APT1 Chinese threat actor conducting computer network espionage activities”. The video is pretty incredible.
At this point you should be impressed by Mandiant and alarmed by the extent of the attacks. But wait, there’s more. In an interview for ABC News, former White House counter-terrorism adviser Richard Clarke says:
The Chinese have attacked every major U.S. company, every government agency, and NGO’s. Their attacking the Chamber of Commerce is part of a pattern of their attacking everything in the US. If you’re working on U.S.-China relations with an NGO, government agency, you can be sure the Chinese are reading your emails and on your computer.
The article, which is describing an attack on the US Chamber of Commerce, says the penetration was so deep that the building’s thermostat was communicating with Chinese servers and one of the local printers began printing in Chinese. But the Chamber of Commerce is not an especially high-value target. Companies like Google, Yahoo!, Ford, and Morgan Stanley, are however. All have been attacked, and everything from top secret engine designs to confidential business documents have been stolen by the Chinese military, leading one US Senator to cal it “the greatest transfer of wealth through theft and piracy in the history of the world.” (Note: that article is from 2011. The problem has grown worse since then.)
I am no foreign policy expert, but I’ll tell you what bothers me. It’s not so much that I am afraid of what the Chinese government is going to do with this information. I think they are cheating and that that is unethical and wrong, but for the most part they are probably using the information to goose their own economy and, quite frankly, if our trading partners get wealthier that’s a good thing. Economics and foreign trade are not zero-sum games. I can’t very well rant and rave in some articles about how patents and copyright restrict the flow of information and then rant and rave in the next about Chinese theft of American intellectual property. Of course they are not the same thing, but there is a connection. As a general rule, the world would be a better-off place if there was more flow of information rather than less. I also think that to some extent this is simply inevitable. When one society is technologically less advanced than another, they get to leap-frog a lot of the growth by copying. Some degree is inevitable. So the theft itself isn’t what concerns me the most (although theft of sensitive military information is particularly unnerving).
What concerns me are what will happen next. The extent of the hacking shows how vulnerable our infrastructure is. So far the Chinese have been interested primarily in theft. What if they were destroying data instead? What if rather than copy the info of the 140+ organizations that they penetrated, they wiped it all? What would that do to our economy? China might not want to do that, or at least not today, but maybe someone else will or maybe the will some other day. Secondly, I’m worried that the response to this could entail militarizing the Internet. From the 1990s until today the Internet has been largely open and free and we’ve all assumed that it was the default nature of the Internet, an immutable characteristic of its very nature. Is it? We might find out. Regardless, however, there’s going to be a definite cost to you and I because as the best hackers in the world (mostly Chinese but also Russian military) find that their tools are no longer succesful against the best-defended networks, they have an incentive to pass those tools onto less players (Iran, North Korea, or maybe even organized crime) who will then deploy the slightly out-of-date, military-grade hacking tools on softer targets. Perhaps like you and me.
This is an arms race but, unlike prior arms races, the weapons aren’t being held in reserve by a couple of tightly-controlled, opposing militaries. Instead, they are proliferating widely, and there’s no telling where the blowback will end. On that note, it’s worth pointing out that the US and Israel have done their fair share to create this nightmare scenario by deploying the first real-world cyberweapons, by which I mean computer attacks that (by accessing industrial control units) were able to create real-world destruction. (The Stuxnet virus messes with the rotational speed of centrifuges to cause real-world damage.) Although 60% of infected computers were located in Iran, the virus has been found in Indonesia, India, Pakistan, and even the US (and others). Iran retaliated by targeting US banks.
What makes all these concerns even more grave, however, is adding nationalism to the mix.
I don’t know if the US has been quashing rumors up until now, and I don’t know if they explicitly or implicitly indicated that Mandiant should go ahead with their reveal. (The Chinese probably suspect that they did, simply because Chinese government-control of the press is so much greater than in the US). I don’t know if this new, in-the-open phase is part of official US policy or not, but I do know that there’s growing legal discussion about the rights of targeted organizations to launch cyber counter-attacks, and that the number of companies offering so-called “active-defense” is increasing. (NPR covered this issue last week, and it’s been featured prominently on legal blog The Volokh Conspiracy as well.) With or without the blessing of the US government, this cyber war is heating up.
Things are probably going to get worse before they get better.